ICT security: far more than just a technical challenge
Information security is not only a legal obligation, but an economic imperative. Incidents not only affect the reputation and trust of brands (such as Google, Swisscom, etc.), but also their value. For companies and public authorities, information is of essential relevance and the basis of any action. Today, information is predominantly processed using information and communication technology (ICT).
Nowadays, business processes are hardly imaginable without IT. Information security deals with the protection of information in these processes. Not only the technological aspect should be considered, but also the analysis of organization, culture and processes.
The terms "IT security" and "data security" are used as synonyms for ICT security. This is the summary of all technical, organisational and personnel measures to ensure the protection of confidentiality, availability, integrity and traceability for the objects of protection (applications, services, systems, networks, data collections, infrastructures and products) of information and communication technology.
Conflicting goals
Security is embedded in the context of usability and cost. The components of this triangle influence each other, and one is generally at the expense of the other. Thus, if security is to be maximized, usability will usually suffer and/or costs will rise sharply. Which component is weighted more for which protected object goals is always a new decision-making process.
The foundation: Information Security Management System (ISMS)
This term refers to a comprehensive, holistic and standardized management system. The ISO 27000 standard describes the family of standards for the introduction and operation of an information security management system (ISMS).
In the ISO standards 27001 and 27002, the basics are elaborated as requirements and guidelines for information security management. The ISO 27001 standard "Information technology - IT security procedures - Information security management systems - Requirements" describes the requirements for an ISMS that indirectly contributes to information security. In doing so, the standard indicates the following objective:
"The information security management system protects the confidentiality, integrity and availability of information through the application of a risk management process, thereby providing interested parties with confidence that risks are being appropriately managed."
This standard describes in generic terms the tasks, responsibilities and authorities of the organization and management in the operation of an ISMS. It deals with the planning, support, deployment, performance evaluation and improvement of the ISMS. Below are specific action objectives and measures that represent the concrete bottom-up requirements for the ISMS.
ISO 27005 is the associated standard that carries out risk management for information security. In it, the classic risk management cycle is expanded to include specific elements that are important for risk management processes. This cycle is aligned with the Plan-Do-Check-Act cycle to provide a complete picture of the risk management system by linking it to the governance process.
ISMS is therefore much more than a technical management system. Every ISMS must be adapted to the size and requirements of a company. Among other things, it regulates processes and competencies, contributes to secure data retention and ensures that compliance requirements are met.
The introduction should be carried out by the management. Among other things, management must provide the necessary human, financial and time resources. Furthermore, the corporate strategy should be aligned with the IT strategy. The leadership role is crucial for success. An IT security culture must be lived and should be part of the corporate culture.
The success factor: IT security culture, integrated into the corporate culture
A major source of danger in the IT sector is often the employee. According to international studies on IT security in the workplace, it is found that only around 50% of employees actively deal with the topic of "information security". Many rely on the employer to provide security and take few precautions themselves. In order to increase awareness, the IT security culture must be an integral part of the corporate culture.
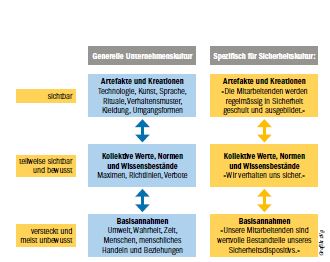
According to Schein1 , corporate culture consists of three levels. On the lowest level are the basic assumptions, which are hidden and mostly unconscious. This includes aspects such as truth, environment, people, actions or (social) relationships.
On the level above, the publicly propagated collective norms and rules, which are partly visible and conscious, are the maxims, guidelines, principles and prohibitions. Ideals, goals and values can be found on this level as well as ideologies - they are verifiable against reality.
At the top of the hierarchy are the visible artifacts and creations. These include organisational structures, processes and observable behaviour, technology, language, clothing and patterns of behaviour.
Schlienger2 states on the subject of "information security culture" that a corresponding concept must include the following characteristics :
- It covers Schein's three levels of corporate culture.
- It influences the employees with regard to the handling of information security.
- It is not anchored as a silo in the company, but is integral, especially in the areas of organization and technology.
- Communication is based on mutual trust, shared understanding of the importance of information security issues and confidence in the measures implemented.
From this, for example, the levels specific to safety culture are derived:
- artifacts and creations: Employees are regularly trained and educated in safety.
- Collective values, norms and bodies of knowledge: We behave safely.
- Basic assumptions: Our employees are valuable components of our security system.
Conclusion
The interaction of a management system in the ICT area with a practiced security culture is a factor that helps to optimally protect the company. The "Corona era", for example, forced companies to make quick decisions in order to increase the capacity of home offices or to make them possible at all. Here, it was hardly possible to comply with all the security regulations in an initial phase. This makes it all the more important, especially in such a situation, to be able to count on risk-conscious employees. Despite great efforts, gaps in ICT security will always exist. It is important to find and eliminate them quickly. Technical measures are central and the company organization must react quickly. In this way, undesirable effects can be minimized and the value of the company can be protected.
This technical article appears in an MQ series contributed by experts from the Risk Management Network: www. netzwerk.risikomanagement.ch









