Home offices under attack: RDP attacks increase by 4,500 percent
The Corona pandemic and lockdowns in the DACH region have led to an explosion in attacks on the Remote Desktop Protocol, according to IT security specialist ESET. But how can so-called RDP attacks be prevented?

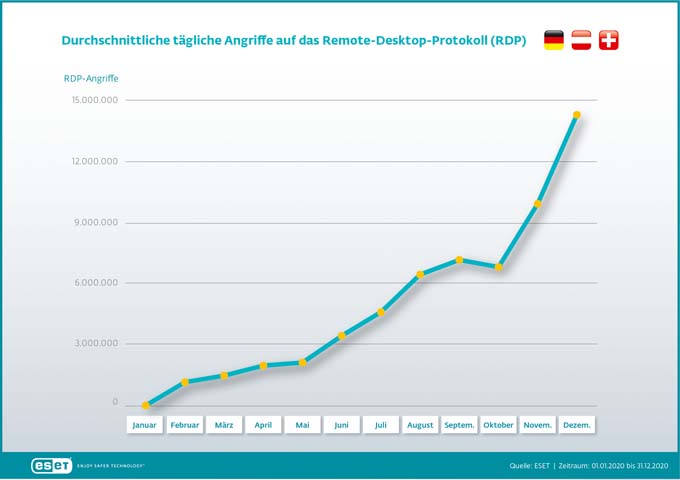
Cybercriminals are massively targeting employees and companies in the home office in Switzerland, Germany and Austria. In December 2020 alone, the European IT security manufacturer ESET recorded an average of 14.3 million attacks per day on the remote desktop protocol (RDP attacks) in these three countries. Especially with the second lockdown following the Corona pandemic and the efforts of politicians to send as many employees as possible to the home office, these attacks have increased by another 110 percent. If criminals gain these accesses, they have wide-ranging access to the corporate network and can thus steal data or introduce malware such as ransomware.
RDP attacks reveal vulnerabilities
"We can answer with a clear YES that home office workstations have been increasingly attacked since the first lockdown. One indicator here are attacks that specifically target the Remote Desktop Protocol (RDP). Many small and medium-sized companies are not optimally positioned for decentralized work and are open like a barn door. Criminals take advantage of this and are very active here," explains Thorsten Urbanski, ESET spokesperson. "With the start of the second lockdown from the end of October, these attacks have increased again by almost 100 percent. This clearly shows that the attacks, which have already increased rapidly since March, have paid off for criminals so far. IT managers should react here immediately and secure their systems as well as accesses more effectively."
Unfortunately, the contemporary protection of the home office workplace is still in its infancy in many small and medium-sized organizations. "Only a third of the companies surveyed in Switzerland allow their employees to access company servers via a secure VPN connection or multi-factor authentication," Thorsten Urbanski continues. "Companies that allow their employees to access the company network via private computers are acting at risk here. This shadow IT is an open invitation for data thieves," summarizes Urbanski.
Strong increase due to home office obligation
In particular, the discussion about a widespread home office for employees led to an increase in RDP attacks in November and December 2020. The peak so far is December with more than 14.3 million attacks daily. From January 2020 (310,000 attacks) to December 2020, that's a 4,516 percent increase. That the attacks have paid off for the criminals is also shown by the 873 percent increase from March last year (1.5 million attacks), with the first measures to contain the Corona pandemic, to December.
What is the Remote Desktop Protocol?
RDP is a protocol developed by Microsoft for remote access to a computer with Windows operating system. The protocol is available in all versions of Windows XP and later. It allows you to share and control a computer or desktop remotely. It is an easy way for companies to allow employees to work remotely. All that is required to connect to an RDP server is a user name and password.
Tips for a secure RDP connection:
- Minimize the number of users who can connect to the company's servers via RDP.
- Allow the use of RDP only if strong passwords and especially modern multi-factor authentication is used.
- Outside your local network, all users should use a VPN gateway (Virtual Private Network).
- Create policies so accounts are automatically logged out in the event of brute force attacks.
- Change the default port 3389 of the RDP protocol to a different number.
Source: ESET









