Global fight against cybercrime shows little progress
General life in 2021 was still very much under the sign of the pandemic. Meanwhile, not only the use of digital services reached a peak. Cybercriminals also seized the opportunity and increased the dangers for users enormously. In its annual Consumer Threat Landscape Report, Bitdefender compiles the results of the data observed in its telemetry for the year 2021.

For 2021, the manufacturer of cybersecurity solutions could see little light and a lot of shadow. There were new negative records in almost all branches of cybercrime. These poor prospects are joined by a new front: unprotected digital identities, which virtually invite criminal activities by hackers due to the careless behavior of consumers.
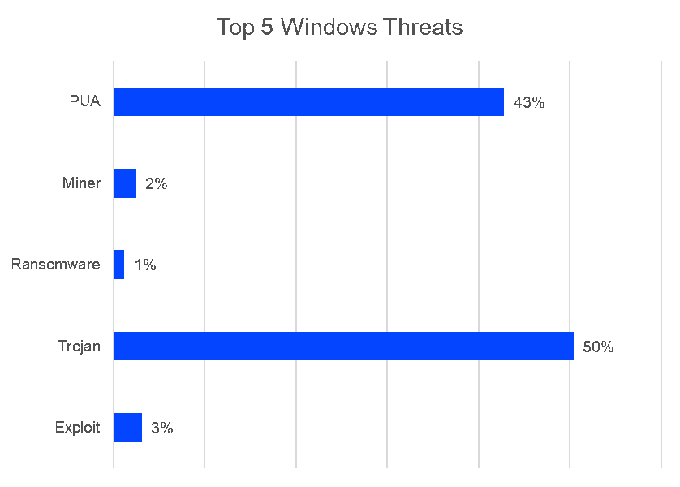
Windows system remain major targets for cybercriminals
Of the many threats that targeted Windows systems last year, five major categories remained unchanged: Exploits, Trojans, Ransomware, Coin Miners, and Potentially Unwanted Applications (PUAs). PUAs in particular seem to be popular in attacks on Windows systems. They account for one-third of all threats directed at Windows systems. On Macs, there is slightly less variation in terms of malware. On macOS, Trojans were analyzed, potentially unwanted applications (PUA), adware and coin miners. The vanishingly small proportion of ransomware, at a full one percent, creates a false picture. It disguises the fact that many solutions recognize a Trojan as the prelude to a larger attack right at the beginning. Trojans are the gateway to prepare the way for subsequent payloads: Such as ransomware, hijacking resources for cryptominer, or even more advanced malware.
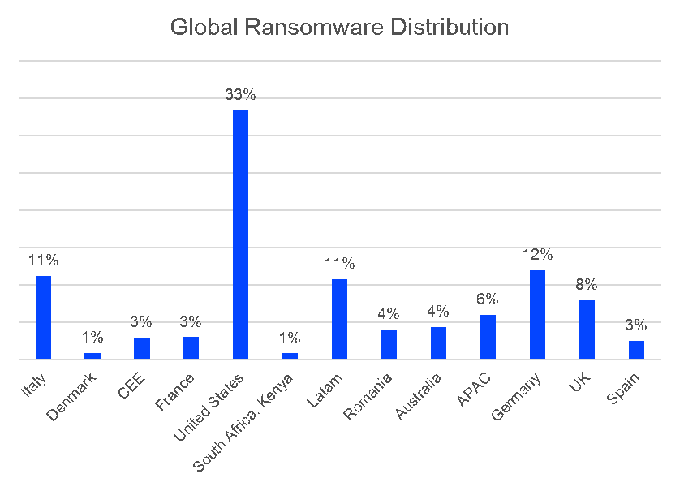
Ransomware: USA is the most important target for attackers
Solar Winds, Colonial Pipeline, Kaseya, and Brenntag are just a few of the big names that have been involved in high-profile ransomware attacks. The extortionists favored industries with high-profile companies and large critical infrastructures - key characteristics that indicate a victim is likely to pay the ransom. The U.S. led the way with 33 % of the attacks, followed by Germany with a notable 12 %. The extortionists focused their activities primarily on countries they believed would be profitable.
IoT devices still a problem
The world of networked smart devices also continues to pose major challenges for IT security. The risk of using them for DDoS attacks is particularly high. Neither the mobile device industry nor the IoT ecosystem have significantly improved their security posture. This means that many of the problems from the past are still present: The operating systems of many devices have numerous security vulnerabilities, are difficult to update. Passwords are still preset and don't need to be force reset. Apparently, IoT security is still not a priority for vendors. A trend seems to prevail: Popular usually means secure. This means that widely used devices from well-known manufacturers are on average more secure than niche products from small manufacturers.
Unprotected digital identities challenge criminal activity
Digital activity has reached an all-time high during the pandemic, with careless consumer behavior further darkening the global cyberthreat landscape. According to Bitdefender Digital Identity Protection telemetry, only 21 % of users have a digital identity with a low level of secrecy. At this level, only one to five pieces of data are exposed online. 62 % of users are apparently not worried about their data being disclosed. More than ten pieces of data about themselves are publicly available. Even though 17 % of users have a medium position with five to ten data items available online, the global average of exposed data items is 26 unique personal data items.
Regardless of the concerns users express about privacy in the digital age, they are dropping their guard and willingly sharing personally identifiable information online. Bitdefender Digital Identity Protection's analysis of telemetry data also shows that URLs (26 %), job titles (21 %) and physical addresses (20%) are among the most vulnerable types of personal data. These records are supplemented by a variety of additional personal information, including usernames, educational background, full names and email addresses, and date of birth.
Android security still needs improvement
With a market share of 70 %, Android dominates the mobile world, exposing it to more risks than iOS, which is second with 27 %. Official Android stores remain a major infection vector, despite their supposed inherent security. Combined with the fragmentation of the operating system, one of the platform's biggest problems, it is easy to understand why Android is plagued by so many threats on a daily basis and why criminals invest time and effort into developing new threats.
A good example is the TeaBot and FluBot campaigns, which have a global reach and use very different methods for organic distribution. For example, TeaBot was spread via fake apps, sometimes even hosted in official stores. The attackers went even further and bought ad slots in legitimate, widely used Android apps that referenced malicious Trojans. For example, it was observed that a QR code reading app hosted on Google Play Store spread 17 different TeaBot variants in a short period of time. Although Google removed numerous malicious apps from its official store several times, the damage had already been done. Samsung's official Galaxy Store was also used to spread malware in the form of Showbox clone apps.
Increased on the road: cryptominer
Resource hijacking by coin miners is becoming increasingly important. Hackers use numerous infection vectors, such as exposed information, potentially unwanted applications, or even warez downloads. Regions that give the hackers rich prey in the form of sufficient computing power are main distribution areas. These include the U.S. with 26 %, APAC with 10 %, and Eastern and Central Europe with 8 %. The EU countries Italy, Denmark, France, Romania, Germany, Spain and the UK account for 34 %.
2022 will be different? Perhaps in certain areas
A look back at the year 2021 shows: The threat landscape is and remains diverse. The spectrum ranges from annoying spam to dangerous malware and digital identity theft. Cybercriminals are extremely creative and constantly on the lookout for new methods to make money with hacks. Computational power, personal identities, and ransomware have been drivers of many attacks. The 2022 Annual Review is sure to provide new insights in this regard. Because the war in Ukraine creates new occasions for spam, as well as phishing. And new motives.
Source: Bitdefender









