Frameworks for IT security
Frameworks are indispensable navigation systems for IT security. Among other things, they facilitate cooperation with business partners and are recognized by the legislator.
Why do you lock the door when you leave the house? Presumably, an open door is seen as a vulnerability that could be exploited by a perceived threat. Depending on what is behind the door, confidentiality, integrity or availability could be compromised. "CIA" is an acronym in the security world for the aforementioned trifecta. If one takes an asset that is worth protecting - e.g. a database with recipes for an Appenzeller digestive - the effects of compromised "CIA" on the database can be assessed (see Table 1).
Compiling the contents of the table is hard work and requires clear responsibilities from business and IT for processes, applications and data. The monetary risk assessment, which is calculated for each threat affecting an asset worth protecting according to the formula probability of occurrence x damage per event, causes difficulties. The monetary assessment is necessary because only risk-reducing measures that cost at most the same as the actual risk cause costs can be considered. The risk assessment and willingness to take risks is subjective and is influenced by:
- The personal risk assessment of the decision-makers
- The risk culture practiced in the company (risk appetite versus risk avoidance)
- The degree of regulation to which the company is subject
- Public opinion
The risks must not exceed the risk-bearing capacity of the company. For this reason, they are mitigated by the following strategies:
- Avoid (company does not operate a business segment due to risk considerations)
- Reduce (introduce IT security measures)
- Shifting (taking out insurance, transferring the risk to business partners)
- Accept (often occurs with residual risks)
Business areas, regulatory requirements, production technologies and IT systems change within the company, and with them the threats, vulnerabilities and risks from an IT security perspective. These must be constantly monitored and their impact on the IT-dependent business processes of a company must be correctly assessed. IT security is a holistic approach that can be well covered by an Information Security Management System (ISMS).
Corporate Governance and IT Security
Information security in the enterprise is a discipline of corporate governance. At the highest corporate level, the information security policy framework is defined, reflecting the importance of IT to most companies. This includes guardrails on the following topics:
- Regulatory requirements
- Dealing with risks
- Safety Principles:
(a) access only to information needed for the job
b) Generally prohibited accesses
- Roles and responsibilities
- Sanctions in the event of infringements
The information security policy legitimises the ISMS and sets the framework for its implementation. It is signed by a board member or the CEO.
Why a framework?
The use of a recognized information security management framework is recommended for the following reasons:
- Process-oriented, lasting improvement
- Recognized by the legislator and known by audit firms
- Templates and tools are available
- Facilitates collaboration with business partners (B2B, sourcing)
Chart 1 shows how the ISMS supports security policy and risk management.
Choosing an ISMS for a company
The environment in which a company operates and the peculiarities of a company influence the choice of ISMS framework. Influencing factors are:
- Regulatory environment: If there are higher requirements for the quality of evaluations and reports on the reliable functioning of an ISMS, a widely recognised framework is used. The degree of familiarity facilitates cooperation with lawyers and auditors.
- Company size: The smaller the company, the greater the pressure to be able to use an ISMS "off the peg" without major adaptations.
- Available resources: The information security policy specifies what information security is worth to a company. In practice, there are great differences in the resources available for setting up and operating an ISMS. The palette ranges from the purchase of ISMS tools to customised in-house developments to outsourcing. However, the responsibility always remains with the company itself (which is sometimes forgotten). Two of the best-known ISMS frameworks will now be discussed.
IT-Grundschutz as a pre-requisite for ISO certification
Based on the recording of all information systems in the company, the structural analysis, the systems and applications found are classified in the protection needs assessment regarding the necessary protection against loss of CIA. The Federal Office for Information Security (BSI) in Germany provides a variety of "building blocks" in which the security measures required for a system (e.g. database) are described. In the modeling, the systems and applications are assigned to the building blocks provided by the BSI. The basic security check delivers as a result the deviations of the desired from the effectively existing security level. The gaps are closed by selecting and implementing the appropriate measures for a particular building block.
The documentation of IT-Grundschutz is freely available, continuously updated and supported by a variety of tools. Companies that implement IT-Grundschutz have made important preliminary achievements for certification according to ISO 27001.
ISO 27001 and 27002
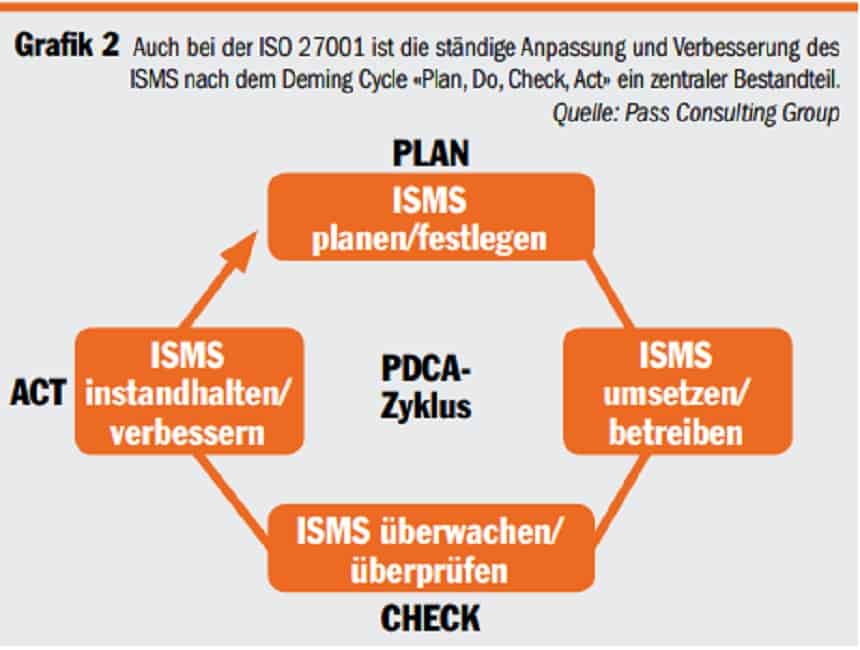
The ISO 27001 standard defines the components and processes of an ISMS. A central component is the continuous adaptation and improvement of the ISMS according to the Deming Cycle "Plan, Do, Check, Act" (see Figure 2). This procedure allows security to be measured, as the goals to be achieved are defined in the "Plan" phase before each iteration.
The ISO 27002 standard (also referred to as Code of Practice, CoP) lists various measures in eleven main chapters in order to achieve the security objectives described. The measures are kept very general and do not have the operational depth of the IT-Grundschutz measures.
Certification
A company can be certified according to ISO 27001 and thus prove the existence of a functioning ISMS to business partners. There is no certification according to ISO 27002, as this ISO standard is a collection of general security measures whose implementation is not mandatory. In addition to the described frameworks with a strong security reference, there are frameworks that deal with the construction of an optimized IT. The IT security framework is then an important component of the comprehensive IT framework.
Both frameworks described below define the organizational structure and associated roles and responsibilities necessary to achieve the process objectives.
COBIT
Control Objectives for Information and Related Technology (COBIT) is an IT governance framework. The business objectives are broken down to IT objectives. The IT objectives result in process objectives for which metrics are specified for control. The framework assigns the processes to the following main IT disciplines:
- Evaluate, specify and monitor
- Adapt, plan and organize
- Build, Procure and Implement
- Provide, operate and support
- Monitoring, evaluation and assessment
COBIT is an excellent framework for organizing IT in such a way that it meets the requirements set during an audit. COBIT was born out of the IT audit environment and developed into a versatile IT governance framework.
ITIL
ITIL is a collection of best practices for implementing IT Service Management (ITSM). The goal of ITSM is the best possible support of business processes by IT. ITIL includes many aspects of IT security and also deals with operational IT security. However, as with COBIT, the focus of ITIL is on building effective and efficient IT that is aligned with business goals. ITIL consists of these disciplines:
- Service strategy
- Service Design
- Service transfer
- Service operation
- Continuous service improvement
There is no ITIL certification, but individuals can have their ITIL skills certified at various levels.









