Best practices for protection against cyber attacks
A novel method of a cyber attack is called "conversation hijacking". This attempts to control the email account undetected: Here, criminals monitor the compromised account to spy on company operations, business activities, payment procedures, and other details.
Cyber attacks consist of different methods. For example, they can initiate conversations based on spied-out information.
However, attackers rarely use the hijacked accounts themselves for conversation hijacking, as the account owner would more easily notice the fraudulent communication. In addition, accounts usually do not remain compromised for a long period of time. "Conversation Hijacking", however, can take weeks of continuous communication between attacker and victim. This is why attackers use email domain impersonation for this purpose, which allows attacks to continue even after the previously hijacked accounts have been backed up and cleaned up.
Criminals then use the researched information from an account takeover to create phishing messages, send them from an impersonated domain, and trick victims into transferring money or updating payment information. "Domain impersonation and conversation hijacking require effort, but are worthwhile from the attackers' perspective because these highly personalized attacks are often more successful than other, less sophisticated phishing attacks.
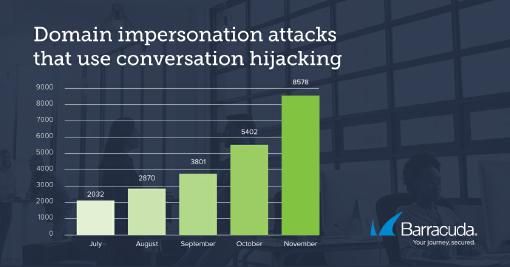
400 percent increase in domain impersonation
Barracuda researchers have observed a sharp increase in domain impersonation used for conversation hijacking. The analysis of approximately 500,000 monthly email attacks showed a 400 percent increase: In July 2019, the emails analyzed included about 500 of these types of domain impersonation attacks, and by November, more than 2,000. While the number of conversation hijacking domain impersonation attacks is small compared to other phishing attacks, these attacks are highly personalized, making them effective, difficult to detect, and costly.
Domain impersonation techniques
For domain impersonation, cybercriminals use so-called typo-squatting techniques such as replacing a letter in a URL with a similar letter or adding a letter to the URL. To prepare for the attack, cybercriminals register or purchase the impersonated domain. Domain impersonation is a very effective attack because the subtle differences between the legitimate URL and the impersonated URL are easy to miss. Sometimes, an attacker also changes the top-level domain (TLD) and uses .net or .co instead of .com to fool victims. In other cases, attackers imitate the external domain of a customer, partner, or supplier.
Best practices to protect against conversation hijacking
Companies can use a variety of security measures and technologies to protect themselves from conversation hijacking:
1. employee trainings and simulation trainings
Education about email attacks, including conversation hijacking and domain impersonation, should be part of security training. Organizations should ensure that employees recognize attacks and know how to report them. Phishing simulations can be used to effectively train users to recognize cyberattacks, verify the effectiveness of training, and identify the users most vulnerable to attacks.
2. protection against account takeover
Many conversation hijacking attacks start with a compromised email account. Organizations should therefore use multi-factor authentication to add an extra layer of security on top of username and password. The security solution should also be able to detect when accounts have been compromised and provide real-time remediation by alerting users and removing malicious emails sent from hijacked accounts.
3. monitoring account logins and incoming mail rules
Organizations should also deploy a security solution to identify suspicious activity, including logins from unusual locations and IP addresses - a possible sign of compromised accounts. Email accounts should also be monitored for malicious inbox rules, as these are often abused as part of account takeovers by cybercriminals. Attackers log into the compromised account, create forwarding rules, and hide or delete any emails they send from the account to cover their tracks.
4. monitoring domain registrations
Furthermore, companies should keep an eye on new domain registrations that could be used for identity theft through typo-squatting techniques. Many companies choose to purchase domains that are similar to their own to avoid potential abuse by criminals.
5. use of artificial intelligence
Attackers adapt their email tactics to bypass gateways and spam filters. Therefore, it is important to deploy a solution that uses artificial intelligence to detect and block attacks, including account hijacking and domain impersonation. This technology should go beyond looking for malicious links or attachments. By using machine learning to analyze normal enterprise communication patterns, these technologies can detect anomalies that indicate an attack.
6. strengthen internal guidelines
In addition, companies should create policies and establish procedures to confirm all email requests for wire transfers and payment changes to avoid costly errors by employees. In-person or telephone confirmation and/or approval from multiple individuals should be requested for all financial transactions.
The above best practices provide a layered security approach for organizations to significantly mitigate the risk from conversation hijacking.
www.datastore.ch/hersteller/barracuda/









