SME demand creates new growth opportunities in the cyber security market
ISG compares the competitive and portfolio strength of service and product providers in Germany and Switzerland. High dynamics in the managed security segment.
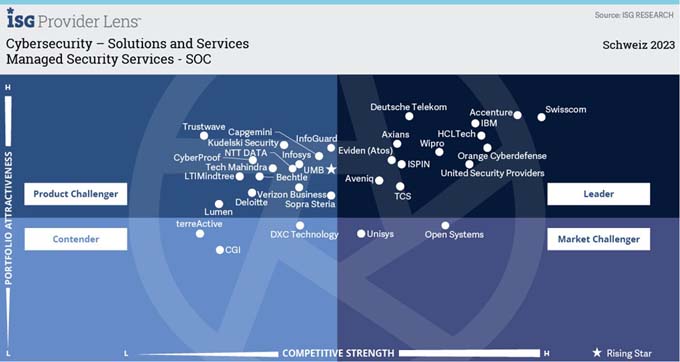
The long-standing success story of the cybersecurity market remains intact. In the face of constantly increasing attack pressure and a worsening shortage of skilled workers, the signs continue to point to growth. Especially in the SME sector. While large companies tend to maintain their already high budgets and increase them slightly overall, it is small and medium-sized enterprises (SMEs) in particular that are generating additional demand. Providers of Managed Security Services (MSS), which have their own Security Operation Centers (SOC), are benefiting the most from this.
This is reported in the new study "ISG Provider Lens Cybersecurity - Solutions & Services 2023", which the market research and consulting company Information Services Group (ISG) has now published in two separate editions for Germany and Switzerland. In it, ISG examines the portfolio and competitive strength of more than 100 service and product providers in the cybersecurity market.
In addition to the MSS-SOC segment, the analysis focuses on six other product areas. In the product area, these are Identity & Access Management (IAM), Extended Detection & Response (XDR), Security Service Edge (SSE) and Data Leakage/Loss Prevention (DLP) & Data Security. In the service area, the two task areas Strategic Security Services and Technical Security Services are added.
Artificial and human intelligence
Cyber security is becoming a key competence. Two factors are driving this development particularly strongly. Firstly, the ever-increasing digitalization of companies is massively increasing the size of attack surfaces and the number of attack vectors. Secondly, the ability of attackers to change their methodical and tactical approach at ever shorter intervals and to use new technologies in the process is also increasing. For example, forms of artificial intelligence (AI). As a result, both the variability and the range of attacks are becoming ever greater. Regardless of this, companies and government organizations are driving forward the digitalization of their processes in order to work more efficiently and in a more customer-oriented manner.
In this mixed situation, it is hardly possible for even large companies to organize the necessary cyber defence completely on their own. Especially as the shortage of specialist staff that can be recruited in the area of cyber security is particularly pronounced. Against this backdrop, the demand for managed security services (MSS) is showing above-average growth rates. The number of providers entering the market with tailor-made solutions is correspondingly high. (MSS service providers manage the operation of IT/OT security infrastructures for one or more customers via a highly specialized Security Operations Center. They rely on best-of-breed security tools and thus cover the entire security incident lifecycle from investigation to problem resolution.
In order to orchestrate the variety of defense mechanisms used and detect relevant attacks early enough, market-leading providers are expanding the use of self-learning solutions that work with various automation, machine learning and AI techniques. "However, this will by no means make the human workforce in SOCs superfluous. Quite the opposite," says study author Frank Heuer, Lead Analyst Cybersecurity DACH at ISG. "After all, sound expert knowledge is needed to set up automation solutions in line with the specific threat situation. It's also about critically evaluating the results of the systems." For example, you need to get as clear a picture as possible of the attacker's interests and then incorporate this picture into the choice of appropriate tactics and the associated defensive measures, Heuer continues.
SME business
ISG believes that SMEs, together with large parts of the public sector, are currently the most interesting growth area for cybersecurity providers. As SMEs have fewer IT security systems overall than large companies, they are forced to upgrade due to the factors described above.
Providers who are able to break down their experience and services to the needs of small and medium-sized enterprises (SMEs) will benefit most from the dynamics of this demand. This requires offers tailored to SMEs. At least as important, however, is the ability of providers to adapt culturally and communicatively to the needs of SMEs and local authorities.
ISG therefore sees market advantages not least for all those providers who have sufficient German-speaking employees. Ideally paired with suitable industry knowledge. In addition, it is still a considerable advantage if the monitoring, control and data processing takes place in regional SOCs. In Switzerland in particular, the unrestricted guarantee of national data protection regulations is one of the most important selection criteria, especially for SMEs.
In contrast, further growth in the large customer segment is currently only possible to a limited extent - after the high investments of recent years. Measured against the IT market as a whole, however, cybersecurity continues to show above-average performance. Especially as a completely new field of activity is emerging that holds considerable disruptive potential, says study author Frank Heuer: "This refers to quantum-resistant data encryption and its continuous further development. In the financial sector in particular, but also in parts of large-scale industry, we are already seeing a noticeable increase in demand for strategic consulting in order to prepare companies' cybersecurity regimes for the threats to data security posed by quantum computers."
Source: www.isg-one.com









